Table of contents
- The history of AES and its developers
- How AES works
- AES decryption
- Strength and security
- AES key lengths
- The role of the S-Box in AES
- Comparison between AES and Triple DES
- Applications of AES
- The security of AES
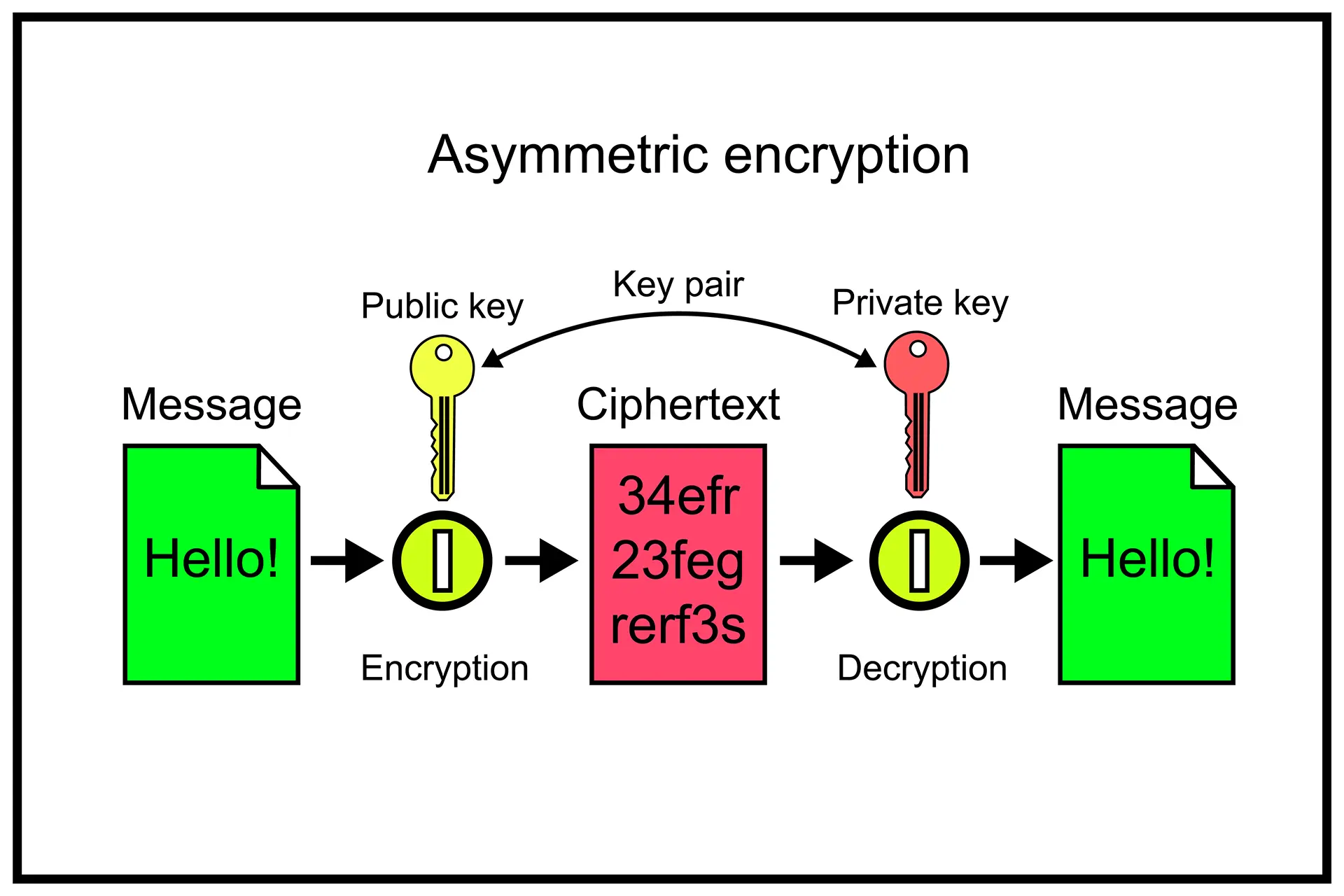
AES encryption, or Advanced Encryption Standard, is a symmetric block encryption algorithm developed to ensure data security. Used in multiple applications, from military communications to the protection of personal data, AES represents one of the most secure and reliable methods for encrypting information.
The history of AES and its developers
AES was developed by Belgian cryptographers Joan Daemen and Vincent Rijmen, and was selected by the United States National Institute of Standards and Technology (NIST) in 2001 as the successor to the Data Encryption Standard (DES).
The main goal was to create an algorithm that was not only secure but also efficient in terms of performance.
How AES works
AES, or Advanced Encryption Standard, is a symmetric block encryption algorithm that operates on 128-bit data blocks using variable-length keys: 128, 192, and 256 bits. The operation of AES can be divided into several main phases: key expansion, encryption cycles, and the final phase.
Key expansion
Before starting encryption, AES performs a process called key expansion. This process generates a series of round keys from the initial key. The original key is expanded into multiple round keys, each of which is used in an encryption cycle.
- For a 128-bit key, 11 round keys are generated.
- For a 192-bit key, 13 round keys are generated.
- For a 256-bit key, 15 round keys are generated.
This expansion is crucial for the security of the algorithm as it makes it more difficult for an attacker to predict the keys used in each encryption cycle.
Encryption cycles
AES performs a series of transformations on the input data through a sequence of encryption cycles. Each encryption cycle includes four fundamental operations:
- SubBytes
In this phase, each byte of the data block is replaced using a fixed substitution table called the S-Box (Substitution Box). The S-Box introduces non-linearity into the encryption process, increasing the algorithm’s resistance to cryptanalytic attacks.
- ShiftRows
In this phase, the rows of the data matrix are cyclically shifted. Each byte in the row is shifted to the left by a certain number of positions. This step helps spread the encrypted bytes throughout the block, increasing security.
- MixColumns
In this phase, the columns of the data matrix are combined using linear mathematical transformations. This operation further mixes the data, ensuring that each byte in the block depends on all other bytes, improving confusion and diffusion.
- AddRoundKey
In this phase, each byte of the data block is combined with a round key generated during key expansion. This step adds an additional layer of security, ensuring that the encrypted data is closely tied to the encryption key used.
The final phase
After completing the required number of encryption cycles (10 for 128-bit keys, 12 for 192-bit keys, and 14 for 256-bit keys), AES performs a final encryption cycle that is similar to the previous ones but omits the MixColumns operation. This final phase produces the final encrypted data block that can later be decrypted using the original key.
AES decryption
The decryption process in AES is the inverse of the encryption process. Using the round keys generated during key expansion, AES applies the inverse operations: InvSubBytes, InvShiftRows, InvMixColumns, and AddRoundKey. This process returns the encrypted data to its original state, allowing for correct decryption only by those who possess the correct key.
Strength and security
The strength of AES comes from the combination of substitution, permutation, key expansion, and bit rotation operations. The block structure and variable key length make AES highly resistant to cryptographic attacks, including brute force attacks, linear and differential analysis. Additionally, the widespread adoption of AES in numerous security protocols and applications attests to global confidence in its ability to protect sensitive data.
AES key lengths
AES keys can be of three sizes: 128 bits, 192 bits, and 256 bits. The security of the algorithm increases with the key length, making it more difficult for attackers to decrypt data without the correct key.
- AES-128: Uses a 128-bit key and requires 10 encryption cycles.
- AES-192: Uses a 192-bit key and requires 12 encryption cycles.
- AES-256: Uses a 256-bit key and requires 14 encryption cycles.
The role of the S-Box in AES
A crucial component of AES is the S-Box (Substitution Box), a substitution table used to replace specific bytes during the encryption process. The S-Box is designed to be highly non-linear, increasing the complexity of the encryption and enhancing the security of the algorithm.
Comparison between AES and Triple DES
Before AES, Triple DES was the standard encryption algorithm. However, Triple DES, which applies DES three times in succession, is less efficient than AES. With its modern design and the ability to use longer keys, AES offers a higher level of security and greater computational efficiency.
Applications of AES
AES is widely used in various sectors. In the United States government, it has been approved to protect information up to the “top secret” classification level. Additionally, AES is implemented in numerous internet security protocols such as SSL/TLS, in Wi-Fi networks through WPA2, and in disk data encryption applications.
The security of AES
AES is considered extremely secure, so much so that there are currently no practical attacks capable of compromising it when used correctly. Its robustness comes from the combination of substitution, permutation, key expansion, and bit rotation operations.
From what has been written, we can conclude that AES encryption represents a fundamental pillar in modern data security. Thanks to its ability to protect sensitive information with 128, 192, and 256-bit keys and its global adoption in multiple applications, AES continues to be a preferred choice for data encryption.
FAQ
- What is AES encryption?
AES (Advanced Encryption Standard) encryption is a symmetric block encryption algorithm used to protect data. - Who developed AES?
AES was developed by Belgian cryptographers Joan Daemen and Vincent Rijmen. - What are the key sizes used by AES?
AES uses keys of 128, 192, and 256 bits. - How does the AES algorithm work?
AES works using a network of substitution and permutation on 128-bit data blocks, applying various transformations with an encryption key. - What is an S-Box in AES?
The S-Box (Substitution Box) is a substitution table used during the encryption process to replace specific bytes. - How does AES differ from Triple DES?
AES is more modern and efficient compared to Triple DES, offering greater security with longer keys and a more advanced design. - Where is AES used?
AES is used in many applications, including SSL/TLS for internet security, WPA2 for Wi-Fi networks, and disk data encryption. - What is the security level of AES?
AES is considered extremely secure, and there are no known practical attacks that can compromise it when implemented correctly. - What is the National Institute of Standards and Technology (NIST)?
NIST is a United States government agency that selected AES as the encryption standard. - What is a symmetric block cipher?
A symmetric block cipher is a type of encryption algorithm that uses the same key to encrypt and decrypt data blocks.

